 I lecture about 50-70 times a year, all over the globe. Of late, my presentations start with an exploration of the Internet of Things (IoT), focused first on my own IoT-enabled life and then addressed to the proliferation of IoT data streams in all our lives. Apart from mobile phones–the apex predators of IoT–discovery from the Internet of Things remains more theoretical than real in civil litigation; and instances of IoT evidence in criminal prosecutions are still rare. That will change dramatically as lawyers come to appreciate that the disparate, detailed data streams generated by a host of mundane and intimate sensors tell a compelling human story.
I lecture about 50-70 times a year, all over the globe. Of late, my presentations start with an exploration of the Internet of Things (IoT), focused first on my own IoT-enabled life and then addressed to the proliferation of IoT data streams in all our lives. Apart from mobile phones–the apex predators of IoT–discovery from the Internet of Things remains more theoretical than real in civil litigation; and instances of IoT evidence in criminal prosecutions are still rare. That will change dramatically as lawyers come to appreciate that the disparate, detailed data streams generated by a host of mundane and intimate sensors tell a compelling human story.
With every disruptive technology, lawyers go through the Four Stages of Attorney E-Grief: Denial, Anxiety, Rulemaking and Delusion. I considered a stage called “Prattle,” but that hit too close to home.
Lawyers confront disruptive technologies by pretending they don’t exist, like those firms who advised clients to steer clear of cloud computing or the multitudes spending millions of client dollars to contort electronic data into printed, paginated documents. When hiding our heads in the sand fails, we worry. In the Anxiety stage, lawyers pen fretful journal articles about the fast-approaching digital Armageddon, exhorting our brethren to “prepare” without practical advice on what to…you know…do. We trot out a Parade of Horribles underscoring the risk and burden flowing from our rendering advice born of fear and ignorance. “Preserve it all,” we counsel, without the fiduciary disclosure of, “because I don’t know what ‘it’ is or how to figure ‘it’ out.”
Anxiety begets Rulemaking, insuring the law marginalizes new evidence and protects parties and counsel from the consequences of business as usual. New rules buy time. The longer lawyers delay compulsory adaption or blunt the consequences of incompetence, the less we are compelled to change.
Rulemaking is a stopgap, of course, because we need evidence to prepare for the tragically tiny potential for trial. Even lawyers can’t observe everyone spending three hours and forty minutes a day on average tapping on mobile screens without it dawning on us that what we need to discover in litigation may be on those phones and in the Cloud to which they connect.
So, rather than buckle down and re-train, we turn to Delusion. The delusions we cherish most are these:
“The big dogs don’t know this e-stuff, and they’re doing fine.”
“I don’t need to understand it; I can hire someone.”
“I’ve made it this far; I can keep faking it.”
When it comes to new information tools, we delude ourselves that whatever we’ve been doing all along MUST be picking up the evidence we’d get from mobile, cloud and IoT. “The same stuff’s in the e-mail and on the network shares, right?” “Surely people half our age use e-mail just like we do?” “And all those apps, they’re just Pokemon Go and Angry Birds.”
Heaven forbid we seek actual metrics to know if our assumptions are borne out by fact. Has your firm or client systematically sampled custodians’ phones and tablets to determine what unique information they hold that is not collected from other sources? No, I didn’t think so.
When it comes to the Internet of Things, the bench and bar are still in Denial, and the doors to Anxiety are open; can Rulemaking be far behind?
But there’s a better way. We can plan, study and prepare to utilize IoT evidence. It’s just data. And when I say, “it’s just data, ” I mean that it’s manageable once you know a little bit about data and databases.
In that vein, here are some thoughts about how the IoT will change civil discovery.
What is the Internet of Things? IoT has been termed an “inextricable mixture of hardware, software, data and service.” I define it as the integration and interconnection of sensors and controls in a broad range of Internet-enabled devices, some paired with living things. It’s the wristband monitoring physical exertion and sleep. It’s the thermostat or appliance controlled by an app. It’s Internet cameras, passive transponders in shoes, biometric sensors in watches, refrigerators that track consumption and tags that track keys and wallets. It’s lights you control with voice commands to Siri, Alexa or Cortana, as well as police body cams, drones and the vast array of cameras and sensors that surround autonomous vehicles. It’s the milk carton that broadcasts its expiration date and the tire that tells you its tread is wearing thin. Too, it’s sensors monitoring a variety of commercial, agricultural, industrial and financial processes. People, plants, animals, tools, inventories: everything that can be instrumented will be, and the data from same will feed algorithms that control processes.
Again, I said people will be instrumented. and, in fact, we already are. Few of us are separated from sensor-rich mobile devices that serve as our digital Boswells. This trend will continue to encompass real time sound- and video recording of law enforcement and all manner of persons whose conduct can prompt loss or liability. IoT will be a routine feature of wearable and implantable medical devices for birth control and pregnancy and to treat, e.g., diabetes, heart disease, obesity, dementia and illness of every stripe. If it moves–a pet, a package, a pest–it will be instrumented and geolocatable.
Increasingly, “fault” will fall on flawed algorithms as much as careless or craven humans. By the same token, the IoT frees humanity from the error and drudgery of humans keeping tabs on a host of conditions, events and movements that machines can track cheaply, relentlessly and precisely.
Depending upon your point-of-view, it’s wonderful or terrifying; but, the one thing it will certainly be is probative, discoverable evidence. There has never been a better time to be a trial lawyer in terms of the richness, variety and accuracy of evidence to help us establish the facts. If you are a lawyer who cares about getting the facts right, rejoice! For lawyers whose trial skills run toward fomenting fear, uncertainty and doubt, the IoT will eventually make your job harder; but, right now, you’re going to have a field day attacking the integrity and admissibility of IoT data.
IP Addressing – How Do We Keep Track of So Many Things? The Internet of Things is made possible by the ability to communicate with each thing, either on demand, at intervals or in real time. This requires that everything be assigned a unique Internet Protocol or “IP” address. Early approaches to IP addressing weren’t conceived with the IoT in mind; so, we almost exhausted the supply of IP addresses when we used 32-bit numbers to denote them in a system called IPv4. A 32-bit (four byte) binary number is customarily expressed as four decimal values separated by periods, so is sometimes called a “dotted quad.”
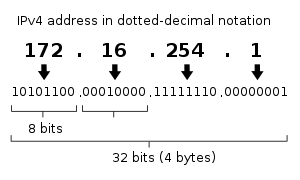
A 32-bit number (2³²) is almost 4.2 billion–a pretty big number, but nowhere near big enough to assign even one unique IP address to every person on Earth. In fact, we ran out of IPv4 addresses on February 3, 2011. Do you remember the chaos that ensued on that date?
Probably not, because the world didn’t notice. Before we ran out of 32-bit IP addresses, a new system called IPv6 was put in place. The address size grew from 32 to 128 bits (16 bytes), thus providing up to 2128 (approximately 340 undecillion) addresses. How big is that? It’s cosmic; equal to the MD5 hash address space, or let’s just say that it’s way more than the number of atoms on Earth. That should hold us for a while.
Because the number space is so large, IPv6 addresses tend to be expressed in hexadecimal values (base16), not decimal (base10) or binary (base2) notation. So, an IPv6 address will comprise eight groups of four hexadecimal numbers separated by colons and with leading zeroes suppressed, e.g., 2602:304:b1b8:25e0:f86f:84a6:8d82:7b86. Hexadecimal notation uses the letters a-f to denote the values 10-15; so, when you see a string of characters composed of 0-9 and a-f, you’re likely looking at hex. Fear not! It’s just a number written in a different notation than the decimal notation we’re used to seeing.
Try This: You can find out the public IP address of your device by Googling, “What’s my IP address?“
Communication with IoT Devices: For the IoT to work, we need more than just a way to uniquely address things, we need a way to talk with them, too. Whether by wire, radio, light or sound, IoT must push and pull data. For example, the last pair of shoes I bought came with an embedded passive near-field communication (NFC) tag. The tag is “passive” because it can’t do anything until it receives power from a nearby electromagnetic field, enabling it to transmit its data (likely a serial number) by modulating the field. Because it needs no power to stand by, the NFC tag can function indefinitely. The tag was designed to combat counterfeit goods; but, the unique signal it supplies could as easily be exploited by a floor mat at Walmart or a multifactor security system at the airport.
Wi-Fi is another common means to communicate with IoT devices, and Wi-Fi connects many of the smart home devices in use today. Wi-Fi demands power-hungry radios, so lends itself to devices connected to AC power or batteries that can be regularly replaced or recharged,
A third conduit is Bluetooth, both “classic” Bluetooth, seen in wireless headsets, or the power-sipping version for data called Bluetooth Smart or LE (for Low Energy). Bluetooth has a limited range (~30 feet); so, Bluetooth devices typically hand off data to an intermediary device that transmits the IoT data to a database via Ethernet, W-Fi or cellular connections or, in the case of a cellphone, populates an app. The Tile locator tags in my luggage use Bluetooth LE to communicate with any nearby cellphone running the locator app. These phones then broadcast the tag’s location to the company selling the tag and ultimately to the locator app on my phone. Because they sip energy, Tile trackers operate for a year using a tiny button battery.
A fourth communication mechanism similar to Bluetooth LE is ZigBee, the IoT technology seen in Phillips Hue smart light bulbs. Up to fifty bulbs speak to a gateway device called a bridge, and the bridge interfaces with the internet, enabling control of the color and brightness of the bulbs via apps on my phone or tablet.
There are other IoT communications mechanisms, including cell systems, optical interfaces like QR codes and even sound-based protocols that allow devices to speak to one-another like R2D2. Typically, IoT ecosystems employ more than one means of communication between the Internet-enabled thing and the end user (e.g., IoT sensor to app via Bluetooth, app to cloud via WiFi or cellular).
Most IoT Data Won’t Reside in the Thing: Apart from notable exceptions like smart phones and cars, most data generated by the Internet of Things won’t be stored within the interconnected “thing” for longer than the interval required to reliably hand it off to a database in the Cloud or an app and to confirm its receipt and integrity. So, no matter how much the IoT proliferates, the burden of preserving and collecting in e-discovery won’t grow commensurate with numbers of devices. The rule of thumb will be, “preserve and collect from the database, not the device.”
Because the U.S. Internet is not uniformly fast and reliable, most IoT devices will require some local storage capability (“cache memory”) that permits the device to buffer the transmission of data to the database or app that serves as repository of the data. Data may also reside on the device as a means to save battery power and bandwidth because a device interrogated at intervals–only awakening now-and-then to send its data–uses less energy than one broadcasting all the time.
The size of the cache or buffer employed will depend on the operating environment, the criticality of the data and the cost and sophistication of the IoT device. The dimensions and form factor of cache memory will be of little consequence as we are able to fashion capacious storage in ever-denser, low-power packages. Which is to say, storage is not only cheap, it’s growing in areal density and, thus, shrinking in physical size. As storage becomes even cheaper, more capacious and compact, devices may end up storing a substantial complement of local historical data as an audit trail and failsafe. Today, we can confidently say, “preserve and collect from the database, not the device;” tomorrow, that could change.
IoT Discovery Practice Tip 1: Ascertain the nature of the ‘things’ connected and the data they collect; but, target your efforts to discover relevant data to the databases and applications where the IoT data lands.
Data or Metadata? Metadata is critical to understanding the context and reliability of IoT data. Unlike a document, spreadsheet, presentation or e-mail message, IoT data streams tend to make no sense apart from the metadata that determines where the data “fits” in an application or database. Sometimes, an IoT data stream will be little more than a bit flag serving to connote a state or status (on/off). Too, IoT streams may include a good deal of data that’s not apparent in the user interface of the target application. So, counsel seeking discovery of IoT evidence needs to be conversant in database discovery (which I’ve addressed in other posts and articles). You will want to discover the composition of the database, its standard reporting capabilities, its data export capabilities and, when these are insufficient, its schema.
Producing parties may have very little insight into the applications they use to collect and mine IoT data. That is, they have no access to a “back end” for phone apps and most cloud implementations. Just because responding parties don’t know (or refuse to learn) about the IoT systems they use doesn’t mean requesting parties can’t do a little homework and craft specific inquiries going to relevant information. Research the IoT device and system. Figure out what you need to know.
Crucially, be specific about the form(s) in which you seek production. Don’t just demand “native with metadata” and expect that’s going to prevent the other side from supplying junk. If they offer screenshots, are you expecting to run word searches against pictures? If they offer an export, will they supply the field and record data needed to make sense of the information? None of these are hard problems, but they demand a little forethought. Hint: learn a little about SQLite, the most widely deployed Structured Query Language (SQL) database engine in the world and the dominant means by which IoT data is stored by phone and tablet apps.
IoT Discovery Practice Tip 2: Research the IoT device and system. Figure out what you need to know, then be specific about the form(s) in which you seek production.
IoT: Curse or Blessing? One difference between the legal industry and the legal profession is that a member of the legal industry just wants to win; a legal professional wants to be on the winning side. Favorable or not, legal professionals want to uncover the true facts underlying a dispute. We want the truth. The inevitable instrumentation of people and products, plants and animals, will be problematic with respect to privacy and cybersecurity; but in litigation, in fact-finding, the precision, objectivity and ubiquity of IoT evidence will be a boon to the pursuit of truth.

Tim Headley said:
Thanks!
LikeLike
Leslie said:
This is a great article. You did an excellent job at breaking down the technology into “human” speak and concepts.
LikeLiked by 1 person
Pingback: The Internet of Things Meets the Four Stages of Attorney E-Grief - @ComplexD | @ComplexD
jimshook said:
Craig, great forward-thinking stuff as always. You make a terrific point about how most of the data will be in a centralized database and not with the device. But of course those databases will not be centralized, so we will be doing eDiscovery and/or issuing subpoenas to many different providers. Taken together, these databases will provide an amazingly comprehensive picture of someone’s day and their activities: where you were, who was with you, what you were doing, etc. And assuming someone wants to subvert that system, swapping (or planting) devices with others could really get weird.
Do you think our existing legal structures (proportionality, authentication, etc) will still serve us well or will we have to develop new ones?
LikeLiked by 1 person
craigball said:
I think we have sufficient tools within the existing Federal rules regime to deal with discovery of IoT. Making the Rules too specific, especially when it comes to preservation or forms, is anchoring them to the past. By the time they’ve gone through the comment and approvals process, they would be woefully behind the times. The light touch inherent to the 2006 approach to amendments was forward-thinking.
Where I think things in the law are out-of-step is with respect to rights and obligations of third-party holders of data. The SCA was written for a POP3 world. After the cloud, it’s a buggy whip in a world of Teslas.
The first step is empowering data owners (and here I mean people, not Cloud providers) to have broad rights of access and portability of their data. No party should be able to dismiss a proper request for discovery by pointing to a third-party holder and saying, “go get it yourself.” “Care, custody and control” extends to the data we entrust to the Cloud and apps. The owner of the data must be obliged to produce it when the law allows, and holders must supply adequate take out mechanisms to support the customer’s legal duties in that regard.
LikeLiked by 1 person
Stefania said:
Reblogged this on these are great days and commented:
Wonderful and comprehensive post (as usual) by Craig Ball.
I truly enjoyed his talk on the same subject at PREX16 in Portland, OR two weeks ago!
LikeLike
Pingback: E-Discovery and the IoT - HARVARD BELL
Pingback: Finding the evidence for hot tub murder and the red-headed children of Greendale | eDisclosure Information Project
Joy said:
Thank you for posting. You shared informative stuff.
LikeLike
Kellan L said:
As we all know Internet of Things will be huge in several ways. Even I agree to you that there will come a day when lawyers will definitely understand the use of IoT and ensure to make it a part of their profession. Keep posting.
LikeLike
Pingback: Dishonesty in politics and law and “useless guff from social media” | eDisclosure Information Project
Pingback: Ethical Implications of Emergent Technologies | New York Legal Ethics Reporter | New York Legal Ethics